Excelitte Cyber Security Digital Products & Consultancy Services
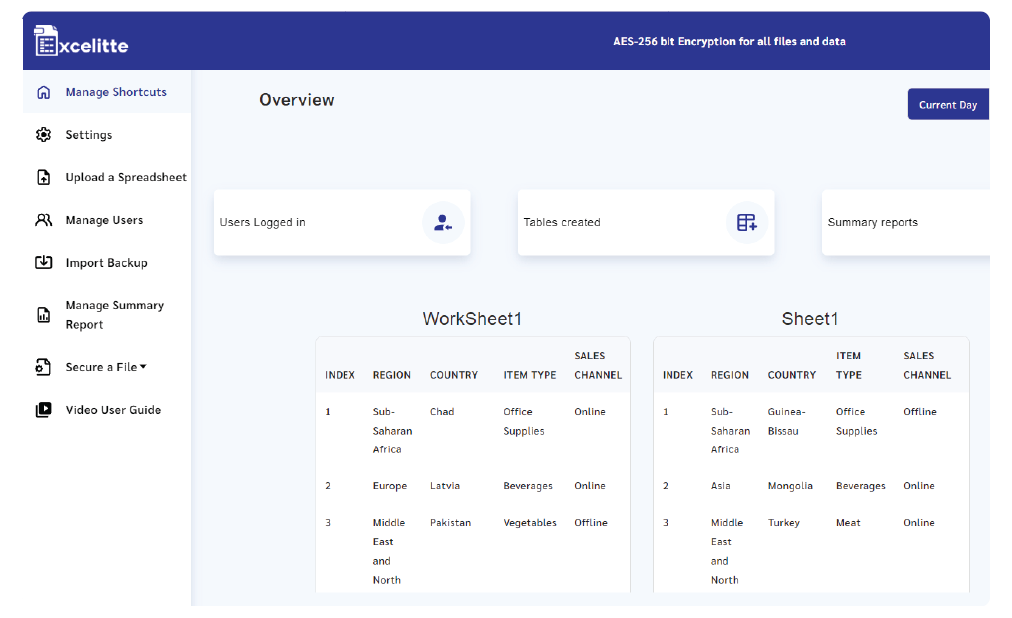
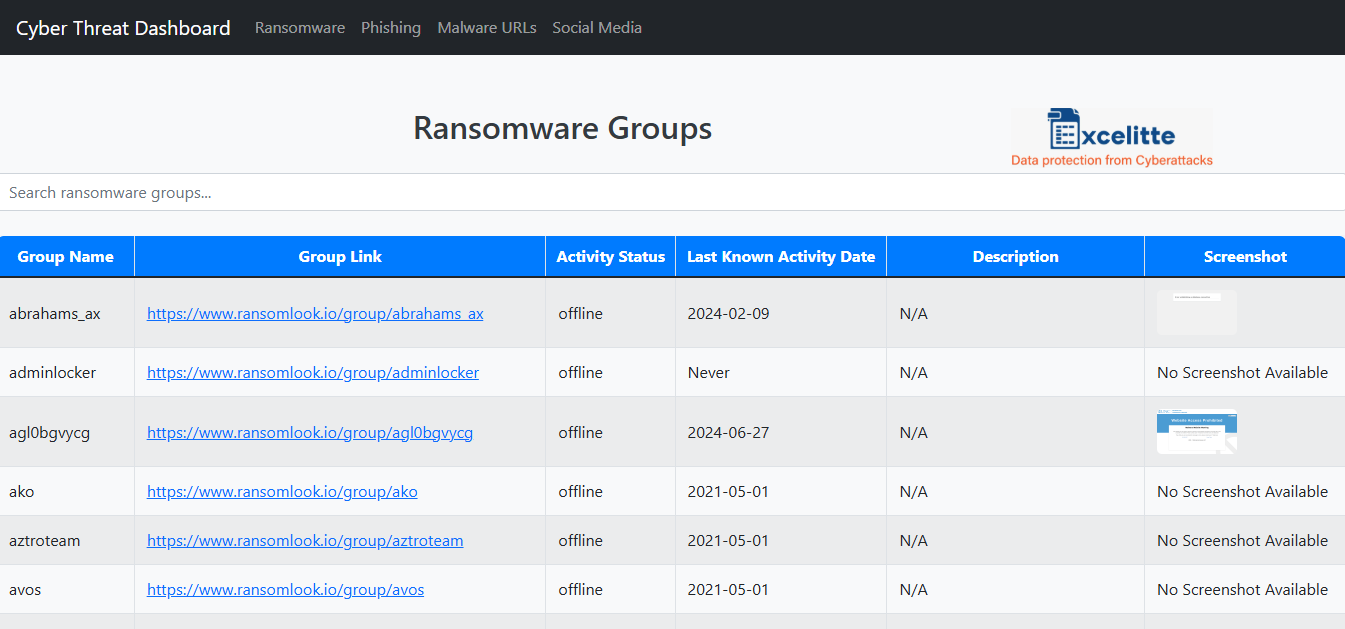
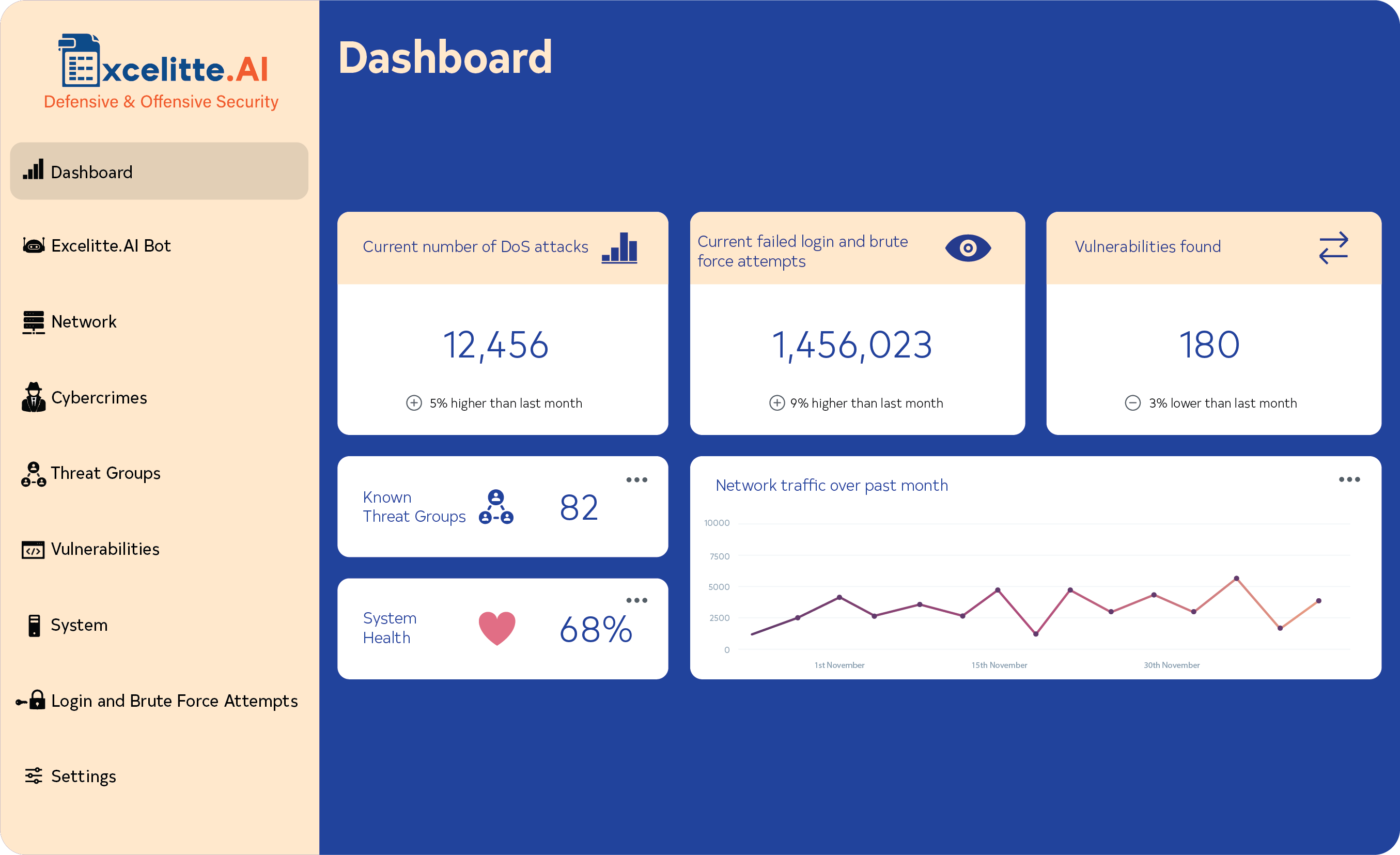
Excelitte is a cloud-based electronic data capture (EDC) and cybersecurity platform designed to convert spreadsheet data and files into a secure, encrypted web-based database application, offering protection against ransomware and unauthorised access.